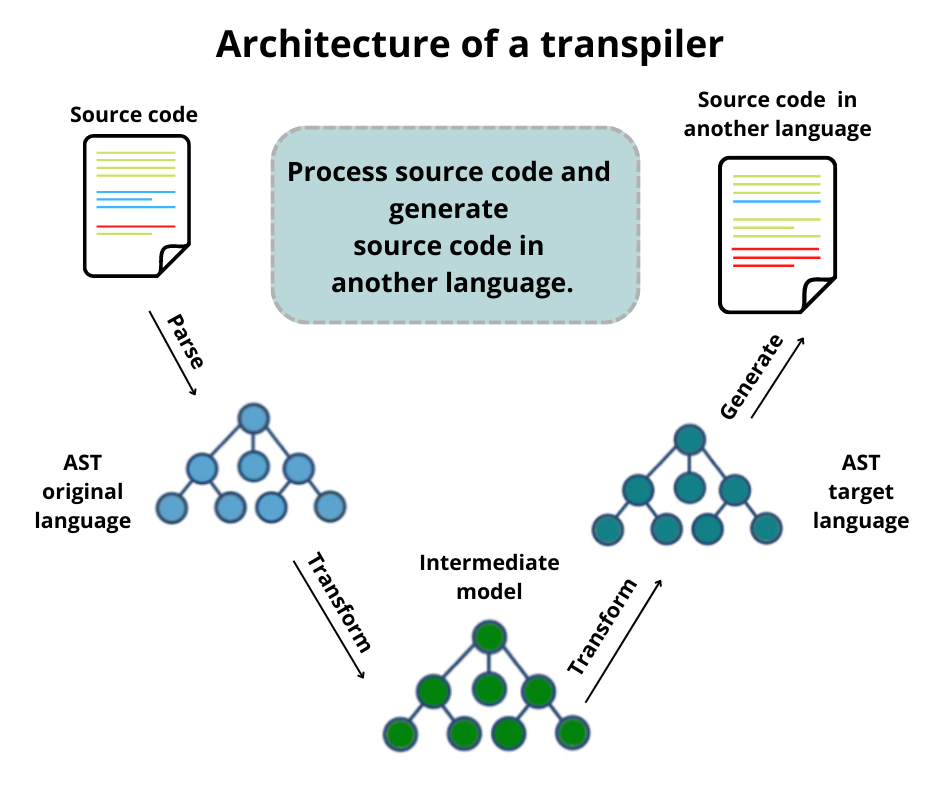
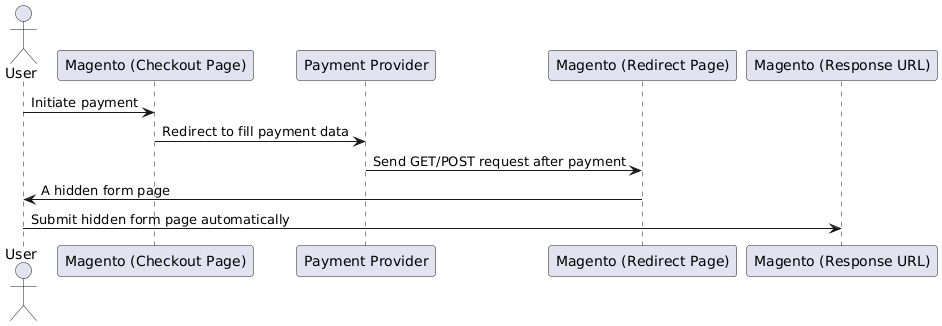
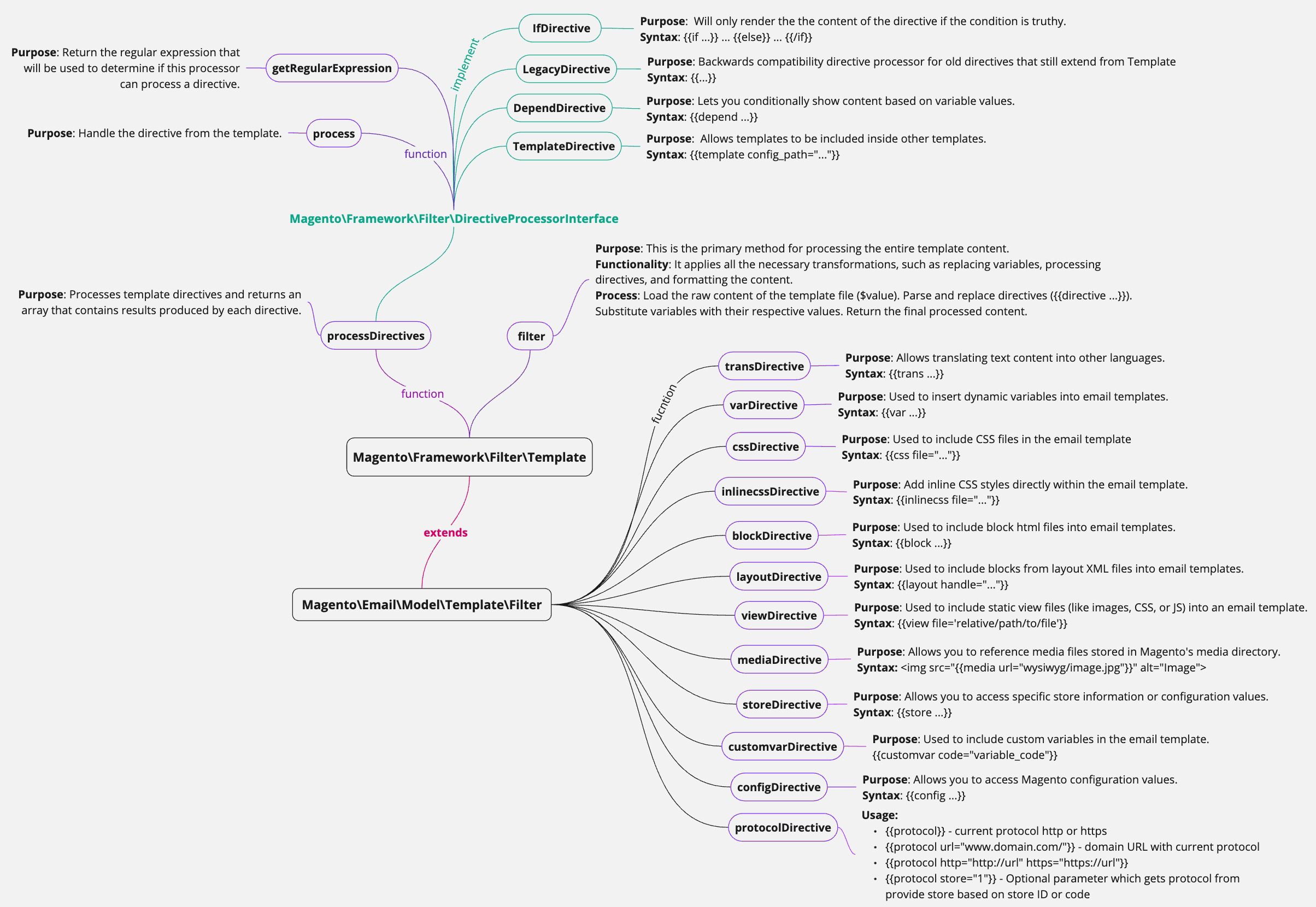
Ensuring the security of Magento stores is a critical part of our work. We’ll explore common vulnerabilities, best practices for securing Magento, and demonstrate real-world examples to highlight potential risks and mitigation strategies.
Security is a shared responsibility. Whether you’re a developer, project manager, or quality assurance specialist, understanding and implementing strong security practices is essential. I look forward to sharing valuable insights and discussing how we can enhance the security of the Magento stores we manage.
Let’s get started and ensure we deliver secure and reliable solutions.
Agenda
Discovering Magento Securities
Discovering Magento Securities
We will disregard the system security aspects, as those fall under the responsibilities of the DevOps team.
Code Security Best Practice
1/ Templates (PHTML and Layout XML)
-
Escape Output: Always escape output to prevent Cross-Site Scripting (XSS) attacks. Use Magento’s escaping methods like
escapeHtml,escapeHtmlAttr,escapeJs,escapeUrl, etc. -
Avoid Direct PHP Code: Minimize PHP code in PHTML files. Keep logic in blocks or view model and use the template for presentation.
2/ JavaScript
-
Sanitize Inputs: Always sanitize user inputs. Never trust data coming from the client side.
-
Avoid Inline Scripts: Avoid using inline JavaScript. If you must use it, ensure it is properly escaped to prevent XSS attacks.
Using herescript
<<<scriptbecause it easier to manage and maintain complex templates, they can indirectly contribute to a more secure codebase. -
Local Storage Security: If storing data locally (e.g., in localStorage), it doesn’t include sensitive information(password, card information).
-
Sensitive Data Handling: Avoid handling sensitive data (like payment details) on the frontend. Use secure, PCI-compliant methods for payment processing.
-
Using Knockout.js Securely: If you are using Knockout.js for data binding, avoid using the
htmlbinding with user-generated content. Use thetextbinding instead:Copy to Clipboard
3/ PHP Code
-
Avoid SQL Injection: Always use prepared statements or ORM methods provided by Magento to interact with the database.
-
Data Validation and Sanitization: Validate and sanitize all inputs. Use Magento’s data validation methods where possible.
-
Error Handling: Handle errors gracefully. Avoid displaying detailed error messages to users. Use logging for debugging.
Restricting access to your Magento Admin Panel
-
2-Factor Authentication
-
Custom Admin URL
-
Avoid using easily predictable admin URLs(e.g:
admin,backend) -
Change the admin url app/etc/env.php or from the admin.
-
-
Enable CAPTCHA
-
Magento Admin Security enhancement from the Stores > Configuration > Advanced > Admin
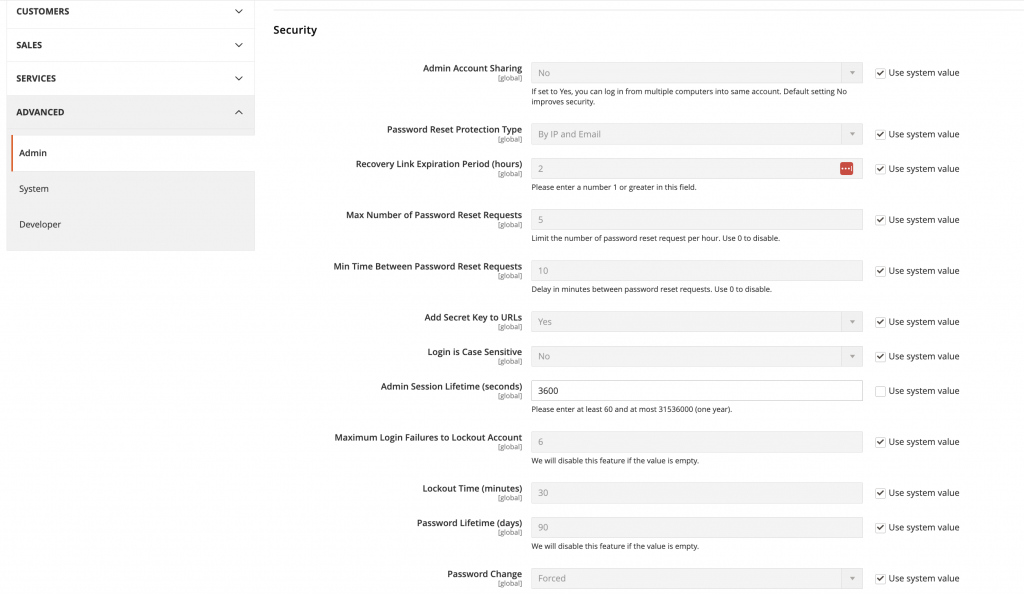
-
We can use Cloudflare – Web Application Firewall (WAF) to limit to the admin access.
Cloudflare (or Fastly)
DDoS Protection: Cloudflare provides robust Distributed Denial of Service (DDoS) protection, preventing large-scale attacks that could take your store offline.
Web Application Firewall (WAF): the Cloudflare WAF protects your Magento store from common web threats and exploits, including SQL injection, cross-site scripting (XSS), and other OWASP top 10 threats.
SSL/TLS Encryption: Cloudflare offers SSL/TLS encryption, ensuring that data transmitted between your users and the server is secure. This can improve customer trust and protect sensitive information.
Bot Management: Cloudflare helps mitigate harmful bot traffic that could lead to account takeovers, spam, and other malicious activities.
Reference: https://www.nexcess.net/help/restrict-magento-admin-panel-access-in-cloudflare/
DEMOS
1/ Example Vulnerability: Cross-Site Scripting (XSS)
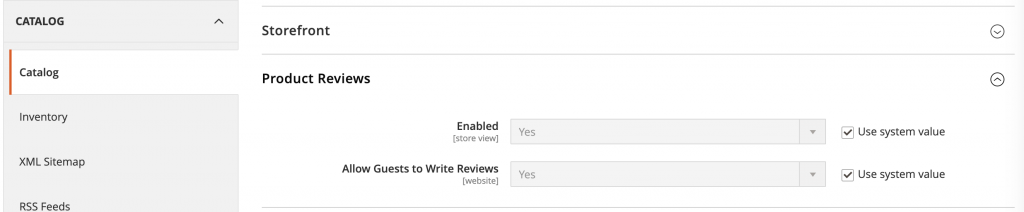
Magento 2.4.6 version: makes sure the Product Review is enabled and allow guests to write reviews
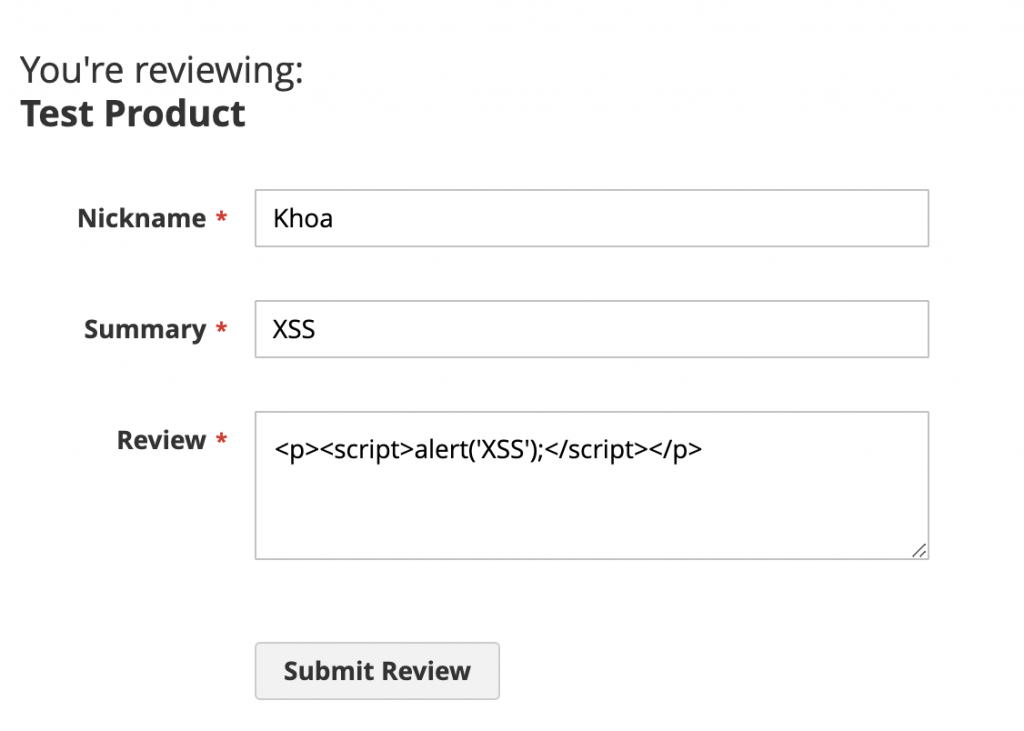
Go to product details page and add a simple XSS script
Remove the nl2br and escapeHtml
Copy to Clipboard
Clean the cache and refresh the product page. The JavaScript alert will execute, demonstrating an XSS vulnerability.
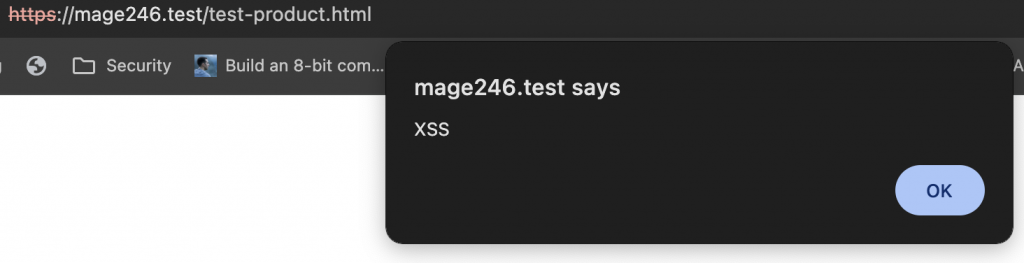
You can put a redirection script to test
Questions:
-
Why does Magento always use the escaper for all text in templates? Not only the user input data but also for all static text.
-
Consistent Output Handling:
-
Using the escaper consistently across all templates standardizes how data is displayed. This reduces the likelihood of vulnerabilities due to inconsistent coding practices.
-
It simplifies the development process, as developers don’t need to remember to escape outputs manually.
-
-
-
When working with headless architecture, Magento will provide APIs for Frontend site. What is the Security best practices on the frontend side?
2/ Ajax call
Create a simple ajax call
Ajax Controller for retrieving the customer review data for a specific product
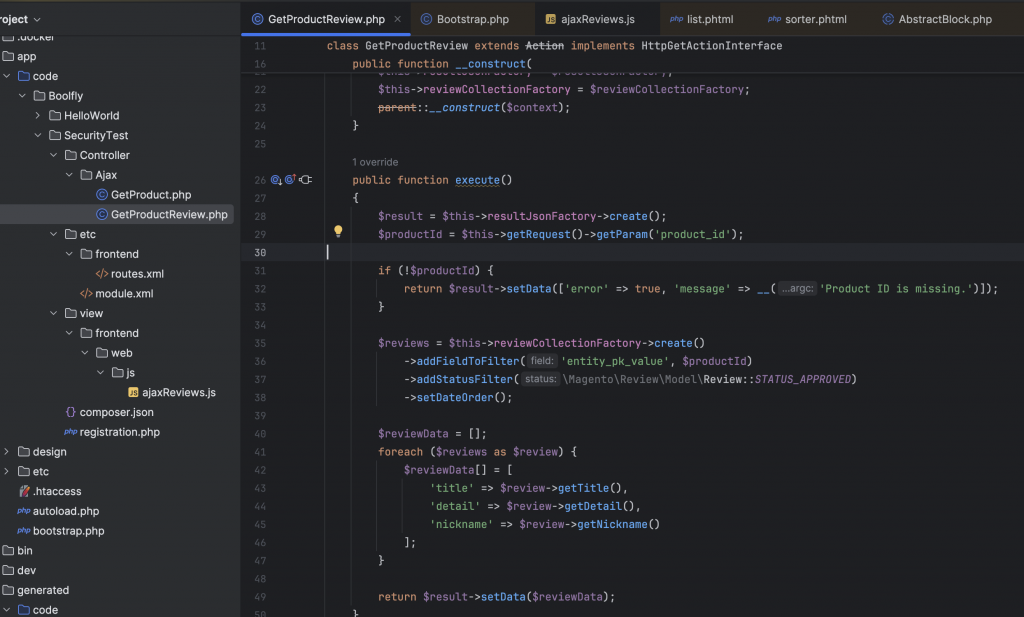
Javascript code
Copy to Clipboard
Go to vendor/magento/module-review/view/frontend/templates/product/view/list.phtml. Add the below code to the bottom of the file
Copy to Clipboard
Clear the cache and open the the product with the review which is containing the XSS script
Copy to Clipboard
You will see the alert after ajax call successfully.
Mitigation
Use the text
3/ SQL Injection in Custom Module
Suppose you have a custom module that retrieves product information based on user input without using prepared statements:
Copy to Clipboard
Copy to Clipboard
This would result in a SQL query:
Copy to Clipboard
Which would return all products.
You can create a simple module with a controller
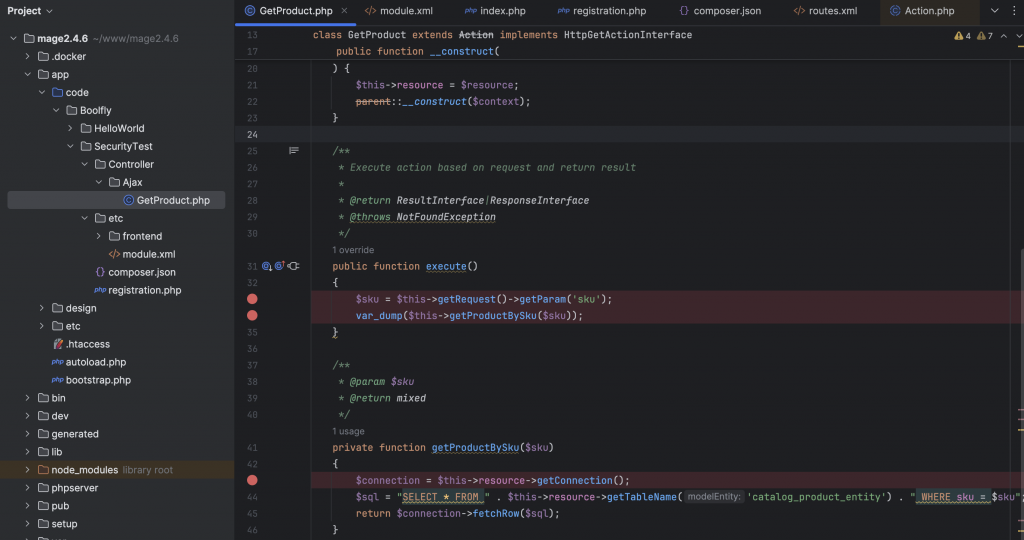
Url encoded value: '' OR 1=1 -- → %27%27%20OR%201%3D1%20--%20
Enter the url with the sku and we can see the result
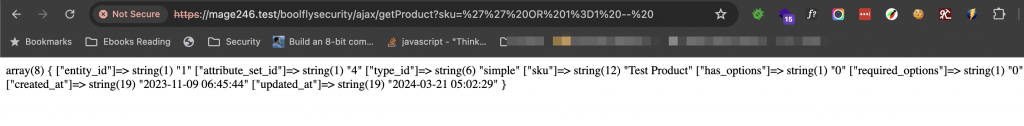
What do you think if it’s the customer data?
Mitigation
Binding
Conclusion
In conclusion, maintaining robust security for Magento platforms is crucial for protecting sensitive customer data, ensuring compliance, and safeguarding business reputations. As an outsourcing company, it’s our responsibility to implement and advocate for best practices such as regular updates, secure coding techniques, proper access controls, and continuous monitoring for our clients.
By staying informed about the latest security trends and threats, engaging in regular code reviews, and fostering a culture of security awareness within our team, we can significantly reduce the risk of security breaches. Security is an ongoing process, not a one-time setup. Let’s commit to making security a priority in our daily workflows to build and maintain secure, reliable, and trustworthy e-commerce environments for our clients.